Microgrid Communications State of the Art and Future Trends Pdf

Advancements and Research Trends in Microgrids Cybersecurity
Department of Electrical, Electronics and Telecommunications Applied science and Naval Architecture—DITEN, Academy of Genoa, via Opera Pia 11A, 16145 Genoa, Italian republic
*
Author to whom correspondence should be addressed.
Academic Editors: Gregory Epiphaniou and Carsten R. Maple
Received: fifteen July 2021 / Revised: 6 August 2021 / Accustomed: ix August 2021 / Published: 10 August 2021
Abstract
Microgrids are growing in importance in the Smart Grid paradigm for power systems. Microgrid security is becoming crucial since these systems increasingly rely on data and communication technologies. Many technologies take been proposed in the last few years for the protection of industrial command systems, ranging from cryptography, network security, security monitoring systems, and innovative control strategies resilient to cyber-attacks. Notwithstanding, electrical systems and microgrids present their ain peculiarities, and some effort has to exist put forth to apply cyber-protection technologies in the electrical sector. In the present work, we talk over the latest advancements and research trends in the field of microgrid cybersecurity in a tutorial form.
1. Introduction
Microgrids can be defined as small-scale, low, or medium voltage power systems with a decentralized group of electricity sources and loads, which can operate connected to or separated ("islanded") from the main power network. To ensure a proper control, microgrids often brand large employ of Data and Communication Technologies (ICT). With the term Smart Microgrids (SM), we refer to microgrids that are based on networked control systems. The command network of smart grids cannot, in general, exist considered as an isolated network: the command network is commonly connected to outside to receive remote commands or let remote maintenance. The used network may include wireless channels, and the grid tin can be geographically dislocated, making some devices physically reachable and prone to attacks. Moreover, the electrical grid is a critical infrastructure, so it can be the target of attackers with huge technical and economical capacities. For these reasons, cybersecurity is a fundamental event to ameliorate the resilience of microgrids. Several attacks against critical infrastructures have been pursued in the concluding few years. 1 of the near dangerous attacks, which gave further visibility to the cybersecurity risks in the industrial sector, has been Stuxnet [one], followed by other complex worms, such as Duqu and Flame [2]. Specifically, in the electrical sector, a severe attack has been the ane against the Ukrainian ability filigree, which caused approximately 225,000 customers to lose power across various areas [3]. Some papers analyze the risks of attacks against Distributed Energy Resources (DER), which may pb to severe outages [4,5]. Researchers all over the globe are making efforts to study microgrids and to build testbeds and demonstration sites. A list of microgrid testbeds has been reported in Reference [6], which besides provides a classification by distribution network and geographical expanse. Notwithstanding, boosted efforts have to be provided in order to implement cyber attacks on real microgrid testbeds.
The process of cybersecurity can be broken down into five sub-problems: Deter, Detect, Delay, Respond, and Recover. To deter deals with discouraging attackers from attempting to gain unauthorized access by implementing measures that are perceived equally too difficult to defeat. To detect is a fundamental stride of the defense-in-depth paradigm, which tackles the problem of recognizing malicious activities as rapidly as possible earlier or afterwards the aggressor has gained access to the organization. Once the assail has been detected, the system should exist able to react against the attacker, delaying the activities of the attacker, and assuasive to take proper countermeasures to defeat the attack and recover from possible damages. The technologies and techniques that will be discussed in this paper address these issues.
Many papers accept analyzed the vulnerabilities of smart grids and, specifically, of microgrids. This newspaper aims to hash out the master contempo advancements and new enquiry trends in the field of cybersecurity of smart microgrids, and the applications in this field of innovative technologies, such as Software Divers Networking, new approaches for intrusion and anomaly detection, and resilient control strategies. The newspaper is structured equally follows. Section ii discusses the state-of-the-art in the field of cybersecurity of smart microgrids. Department three analyzes techniques that can be applied to microgrid advice protocols and highlights possible vulnerabilities and countermeasures, with a particular focus on the part of IEC 62351 to secure microgrids. The residuum of the paper focuses on technologies that can provide great benefits to the security of microgrids merely that are all the same a inquiry field. Section four discusses the application of the Software-Defined Networking (SDN) prototype to enhance microgrid resilience and cybersecurity, while Section 5 considers the implementation of Intrusion Detection System (IDS) techniques on electrical devices with a special attention to Host-IDS (HIDS). Section 6 focuses on physics-based bibelot detection algorithms that can be practical to ability systems. The main works on control strategies that can be implemented in distributed free energy resources in order to amend the resilience to cyber-attacks and the availability of the whole organization are summarized in Section 7. Conclusions are drawn in Section 8.
2. Cybersecurity in Smart Microgrids
Smart Grid is the new paradigm for ability systems. Fifty-fifty if in that location is no unique definition, the European Union Commission Task Strength for Smart Grids provides the following one: "A Smart Grid is an electricity network that can toll-efficiently integrate the behavior and actions of all users connected to it—generators, consumers, and those that do both—in order to ensure economically efficient, sustainable power organization with low losses and loftier levels of quality and security of supply and condom. A smart grid employs innovative products and services, together with intelligent monitoring, control, communication, and self-healing technologies".
It is hard to evaluate the cybersecurity risk of smart grids due to the huge variety of Information and Communication Technologies that tin can be used to reach a wide ready of tasks. For example, the National Electric Sector Cybersecurity Organisation Resource (NESCOR) identifies six scenarios in the power system where main failures related to cybersecurity threats [vii] tin happen: Advanced Metering Infrastructure, Distributed Energy Resource (DER), Wide Area Monitoring Protection and Command, Electric Transportation, Demand Response, and Distribution Grid Management. Each technology has its own peculiarities impacting differently on the whole power system. Several papers accost the issue to survey the main vulnerabilities and threats of the electric ability system: [viii,9,10]. Reference [5] discusses the architecture of power systems with a high penetration of DER and related cybersecurity issues and summarizes attack scenarios against DER likewise because set on prevention, detection, and response measures specifically designed for DER.
A Survey on Cyber-Security of Smart Microgrids is proposed in Reference [11], where a sample of recent cybersecurity projects, a review of cybersecurity standards and protocols for power systems, and a classification of attacks with related bear on and mitigation strategies are provided. Reference [11] provides a curt overview of some technologies that will be further discussed in this paper. Reference [12] addresses the cyber-physical security in power systems by focusing on microgrids and their control structure. Papers including an analysis at a glance of the most promising recent technologies that tin can meliorate the cybersecurity of smart microgrids are still missing at the all-time knowledge of the authors of this paper.
3. The Activity of IEC 62351
Control networks in Supervisory Control And Information Acquisition (SCADA) systems were typically realized past using merely proprietary solutions. Several application protocols were developed, each targeting specific communication constraints required by the control systems. The demand of remote control and the advances in computer networks led to the blending of traditional control networks with mod Internet. Consequently, control systems inherited security vulnerabilities that threatened the modern cyberspace [13]. In the electrical sector, broadly employed protocols to communicate data and control information are Modbus, DNP3, IEC 60870-5, and IEC 61850. In particular, although developed for substation automation, IEC 61850 suite is exploited for smart microgrids [14]. Abstract information models defined in IEC 61850 tin be mapped to unlike protocols, such as Manufacturing Message Specification (MMS), Generic Object Oriented Substation Event (GOOSE), and Sampled Measured Values (SMV), which can run over TCP/IP networks or over substation LANs by using Ethernet.
As said, severe vulnerabilities affect these protocols. Different papers show possible attacks at these protocols and the related bear upon. In Reference [fifteen], vulnerabilities of GOOSE are tested past using existent-fourth dimension simulation and manufacture standard hardware-in-the-loop emulation. Reference [sixteen] shows how an assailant can launch a Man-In-The-Eye attack on the MMS communications of a photovoltaic inverter installation by using ARP spoofing.
Some of these vulnerabilities are currently addressed by IEC 62351, which is a standard developed by WG15 of IEC TC57. The main purpose is to address the problem of security of TC 57 series of protocols including IEC 60870-5, IEC 60870-six, IEC 61850, IEC 61970, and IEC 61968 series. Currently, the standard is composed of 18 parts listed in Table 1.
IEC 62351 series does non provide but cryptography for common electrical control organisation protocols. Information technology too defines cybersecurity requirements to implement security technologies in the operational environment, including objects for network and system management, role-based admission control, cryptographic cardinal management, and security event logging.
IEC 62351 offers a list of guidelines for protocols security and a framework for secure operations. It is designed to be referenced past other standards, not used directly. For instance, IEC 62351-3 specifies how to provide confidentiality, tamper detection, and message level authentication for SCADA and telecontrol protocols, and how to secure TCP/IP-based protocols through constraints on the specification of the messages, procedures, and algorithms of Transport Layer Security (TLS) 1.2 according to RFC 5246. However, its implementation in actual operation scenarios, such as overcurrent relay coordination or DER management systems, is open to interpretation. For example, IEC 62351-vi standard stipulates the use of digital signatures to ensure integrity in IEC 61850 message exchanges, but the digital signature requires a high computational time with consequent problems for applied implementation in GOOSE messages. For these reasons, IEC 62351 cannot offering a strict procedure for the implementation of cryptography techniques.
Reference [17] provides an assessment of the security of IEC 62351 and concludes that, although the standard contains some inaccuracies and unconventional choices, and does non consider new cryptographic algorithms that could provide the same security guarantees at a lower performance cost, the standard provides a significant security comeback, by assuring authenticity, integrity and confidentiality of information. Some recent papers accost the outcome of IEC 62351 implementation. A complete evaluation of security mechanisms for IEC 61850 message exchanges, including GOOSE, SV, routable-GOOSE (R-GOOSE), routable-SV (R-SV), MMS is presented in Reference [18]. The implementations of IEC 62351-four Security for IEC 61850 MMS Messages has been discussed in Reference [19]. An assay of the implementation of Message Authentication Lawmaking (MAC) Algorithms for GOOSE Message Security according to IEC 62351 has been presented in Reference [20]. An assay and functioning evaluation of the implementation of IEC 62351-6 probabilistic signature scheme to secure GOOSE Messages is contained in Reference [21].
For these reasons, the implementation of IEC 62351-based techniques to secure common microgrid protocols will represent a pregnant improvement. Notwithstanding, some effort has to be invested in gild to use the standard in different contexts.
four. Software Defined Networking
Software-Divers Networking (SDN) applied science is an approach to network management that enables dynamic, resource-efficient, and programmable network configuration in order to better network operation and monitoring. SDN centralizes the network intelligence in one network component by decoupling the forwarding process of network packets (data airplane) from routing procedure and control actions (control plane). SDN is a useful solution to meliorate the performance, safety, and security of different types of networks, including smart grid control systems. OpenFlow is the about popular standard/protocol to substitution messages betwixt control and data planes in SDN [22].
A comprehensive survey of SDN-based smart grid communication is presented in Reference [23]. Applications include Substation Automation, Advanced Metering Infrastructures, Phasor Measurement Units, and as well microgrids. Many papers focus on the benefit of SDN in isolating unlike traffic types/applications, prioritizing traffic, assuring resilience and fast failure recovery, and for the implementation of virtual network slices [24].
SDN also has interesting applications for the security of Industrial Control Systems (ICS), especially for incident response. It allows increasing the resiliency of the control system, thanks to the possibility to dynamically re-configure the network after the detection of a fault or of a compromised device, allowing it to operate fifty-fifty in degraded conditions. This is specially useful for control networks within critical infrastructures, which crave extremely high availability. Reference [25] discusses how SDN and Network Function Virtualization (NFV) technologies tin can help blueprint automated incident-response mechanisms for ICS and also describes a paradigm to evidence the feasibility in a scenario that uses Programmable Logic Controllers (PLC) managing a classical tank-filling control system. Reference [26] studies the applicability of emerging technologies in the area of IP networks, including SDN, NFV, and next generation firewalls, to secure ICS. Reference [27] proposes an attack detection and localization algorithm and designs an intervention strategy in the networked robot control field. A software-defined security approach to secure field zones in ICS is shown in Reference [28]: it consists of a hybrid anomaly detection module that inspects anomaly behaviors in network communications and concrete process states. It proposes a multi-level security response module that allows isolating any compromised zone.
Microgrids could significantly do good from cocky-healing network management, which includes simply is not limited to [29]:
-
quick reset and reconfiguration of switches in gild to isolate suspicious devices in the microgrid;
-
establishment of application-specific filtering operations in the switches located close to attack sources; and
-
on-demand path establishment for control commands to shrink assailant'southward operation time window.
SDN allows verifying the entire advice network concerning security policies (e.thou., access control) and network situations (e.g., loop-liberty and congestion-freedom). SDN allows likewise directly implementing a Network Intrusion Detection System (NIDS) within the SDN controller, even if such implementation may introduce a latency time that could be incompatible with the allowed latency in a microgrid environment [30]. The awarding of the SDN paradigm in microgrids may comprehend both security and control applications, as shown in Figure 1.
Focusing on security applications, the SDN paradigm has been applied in different scenarios, to address attacks that target unlike communication layers. Reference [31] proposes an SDN architecture able to switch between wireless and electric line communication to go on proper control within a direct current microgrid under a Deprival of Service (DoS) attack. Reference [31] proposes an compages that exploits SDN control airplane bulletin exchanges over the ability charabanc, allowing the reconfiguration of the information plane connections. In this way, all generators in the microgrid operate as either voltage regulators (agile agents) or current sources (passive agents), with their operating modes existence determined by software-divers controls supported past the control plane communication performed over the power bus. An SDN-based attack detection to protect networked microgrids from cyber-attacks based on a botnet that targets inverter controllers of DERs is presented in Reference [32].
Of course, the implementation of such an compages tin can farther augment the assail surface [33]. All the same, SDN technologies can meliorate the overall microgrid resiliency towards cyber-attacks, faults, or natural events, thanks to the offered customizable network configuration power. It is a promising research field with firsthand practical applications.
5. Intrusion Detection Systems
Intrusion Detection Systems (IDS) are devices or software applications that monitor a portion of the systems and effort detecting malicious activities and policy violations. IDS can be classified from different viewpoints. Nosotros tin identify two big families:
-
Network Intrusion Detection Systems (NIDS) that analyze network traffic nerveless from one or more points of the communication network; and
-
Host Intrusion Detection Systems (HIDS) that analyze the activity of a single host (i.due east., a final) of the network.
Other classifications tin be based on the strategy used to discover the malicious activity (signature-based or bibelot-based) or on the action that the system implements afterward detecting an attack (IDS can exist purely passive or block traffic flows/applications, unremarkably referred to every bit Intrusion Prevention Arrangement (IPS)), every bit shown in Table 2.
Different NIDS solutions specifically designed for ICS protocols have been proposed in the literature and are also available every bit commercial solutions. NIDS are usually passive elements of the network to avoid them significantly slowing downwards the responses to attacks. It would exist dangerous to implement an active element in a safety-critical control network due to the possible loftier false positive rate that would affect the whole system safety.
In the It field, two common HIDS solutions are Open Source HIDS SECurity (OSSEC) and Tripwire. OSSEC is a free and open-source HIDS that supports a wide range of Operating Systems (Os), while Tripwire is a commercial solution. These solutions combine passive actions performed periodically in lodge to not affect the organization functioning, such equally the identification of unauthorized file modifications (through, for instance, file integrity checking past using checksum databases), of malicious processes, and of log behaviors (for instance by monitoring specific parameters), and agile capabilities, similarly to host firewalls that allow blocking unauthorized network communications past adding firewall rules.
A further improvement in the field of HIDS is online intrusion detection (or "existent-fourth dimension" or "in-line" intrusion detection). Real-time HIDS analyze different features of the host, including OS aggregated behavior, such every bit CPU and retentivity metrics, shell commands, and system calls; application data, such as loaded modules and libraries, programming code, and processes; user behavior and host network information, such as physical and logical interfaces, and their configuration, as well every bit network packets [34].
All the same, in guild to implement HIDS in ICS devices, further considerations are necessary. Two major challenges have to be faced: the time operation in devices with astringent latency requirements and low computational power, and the risk related to the implementation of agile HIDS.
Attributes that a HIDS suitable for ICS application should include are [35]:
-
Configurability: capability to exist configured as specified by the requirements of the target system;
-
Configuration and Knowledge Security: HIDS configuration and used data should exist protected against unauthorized access and modifications;
-
Resiliency: HIDS action cannot affect the availability of the device;
-
Low Performance Overhead: the execution of the HIDS on the target device should non negatively influence the performance of the underlying organization;
-
Depression Detection Time: detection and response to intrusions should be as fast equally possible; and
-
Interoperability: the HIDS should exist able to collaborate with other technologies, such every bit Security Information and Effect Direction (SIEM).
In general, regarding embedded industrial devices, operational requirements for industrial environments, such as real-time capabilities, and availability must be ensured, fifty-fifty in the context of a cybersecurity action. Domain specific standards, guidelines, and recommendations that tin can be applied for specific industrial sectors must exist considered to address this consequence.
In a microgrid environment, the nigh time-critical devices are PLC, Remote Terminal Units (RTU), and, in particular, electrical protections.
To give a few examples about electrical protections:
-
IEC 60834 requires that the latency of the transmission and reception of a control signal related to a protective activeness has to be lower than 10 ms, while IEC 61850 imposes a latency lower than 3 ms;
-
IEEE 1646-2004 requires data on protective actions to be exchanged by the devices inside the same substation in a time lower than a quarter of a period (i.e., 5 or four ms depending on the 50 or 60 Hz frequency); and
-
less stringent limits (betwixt 8 and 12 ms) are required for the exchange of information on protective actions with devices outside the substation.
Virtually PLC and RTU are based on Real-Time Operating Systems (RTOS) [36]. The main characteristic of RTOS is the way they handle operations and resources, completing and executing tasks within a defined fourth dimension frame due to their optimized architecture and features. Multi-tasking is still possible, thanks to task scheduling. RTOS handle priority: each task has a priority, and the chore with the highest priority has a preference of execution, even if it is necessary to forestall a lower-priority chore from being executed.
Real-Time HIDS are sometimes implemented as a kernel module in Linux-based operating systems. This blazon of implementation can bear on the device operation. For this reason, even if some papers already propose HIDS specifically designed for ICD devices [35], farther effort has to be put forth to verify the applicability of these solutions to electrical devices within a smart microgrid.
6. Physics-Based Bibelot Detection
Cyber-attacks against industrial systems aim to alter the physical behavior of the usual organisation process. In cyber-physical systems, the concrete evolution of the organization state has to follow immutable laws of nature. For this reason, some papers propose to add a further line of defense in ICS, represented by algorithms able to speedily discover aberrant physical behaviors based on measures extracted from the industrial process. For example, the concrete properties of the process can be used to create models that, in plow, may be exploited to bank check if information coming from sensors is consistent with the physical laws and the expected concrete behavior of the system and if the sent control commands correspond to a real need or if they derive from an artificial modification of the measure. Applications include not only smart microgrids but also water control systems, power grids, chemical procedure control, and medical devices, amid many others.
Monitoring the "physics" of cyber-concrete systems to detect attacks is a growing area of research. Reference [37] presents a review of physics-based bibelot detection schemes based on a unified taxonomy. These organization can exist categorized under different viewpoints. Two possible categories are: algorithms based on pre-defined models and algorithms based on Machine Learning (ML). State estimation models for power systems, which exploit the known equations of power transmissions, belong to the first category. However, for some circuitous systems, such every bit DES, to write a airtight-form equation that takes into account all the measured parameters can exist difficult. In these cases, ML can aid develop anomaly detection algorithms, even if the great disproportion between bachelor information of normal and aberrant behavior typical in cyber-physical systems can limit the application of ML-based schemes. Peculiar anomaly detection techniques are used to address this issue [38].
Physics-based Anomaly Detection Systems notice many applications in the smart microgrid environs. After the evolution a consensus-based distributed voltage control architecture of isolated DC microgrids, an belittling consistency-based anomaly detection mechanism based on variables associated with the proposed algorithm is presented in Reference [39]. Reference [40] proposes an IDS congenital on the combination of network information, together with power arrangement and control information. Reference [41] shows a contextual anomaly detection method based on an artificial neural network and its employ in the detection of malicious voltage command actions in the low voltage distribution grid. Reference [42] presents a high-dimensional data-driven cyber-physical attack detection and identification based on electrical waveform data measured by waveform sensors in the distribution power networks. Reference [43] describes an anomaly detection algorithm to reveal attacks on PhotoVoltaic (PV) systems, such as PV disconnect, power curtailment, Volt-var attack, and reverse ability flow in a portion of the distribution grid with a sufficient percentage of DER penetration. This approach exploits semi-supervised ML algorithms, such equally Neural network autoencoder, I Class Support Vector Machine (SVM), Isolation Forest, Random Forest with constructed corruption, Primary Component Analysis (PCA) with convex hulls, and Inverse-PCA techniques. An approach based on a fully-continued neural network autoencoder to detect cyber-attacks within a PV system is proposed in Reference [44]. A deep learning scheme composed of long and short term memory-stacked autoencoders and convolutional neural networks followed by a softmax activation layer is used in Reference [45] for fault detection in a air current turbine.
Physics-based anomaly detection systems represent an interesting field of research, in particular for DERs. Farther research studies should include a comparing between the huge multifariousness of anomaly detection techniques and should test the proposed approaches against new malicious activities that can be imposed on distributed electric generators.
seven. Resilient Control Strategies
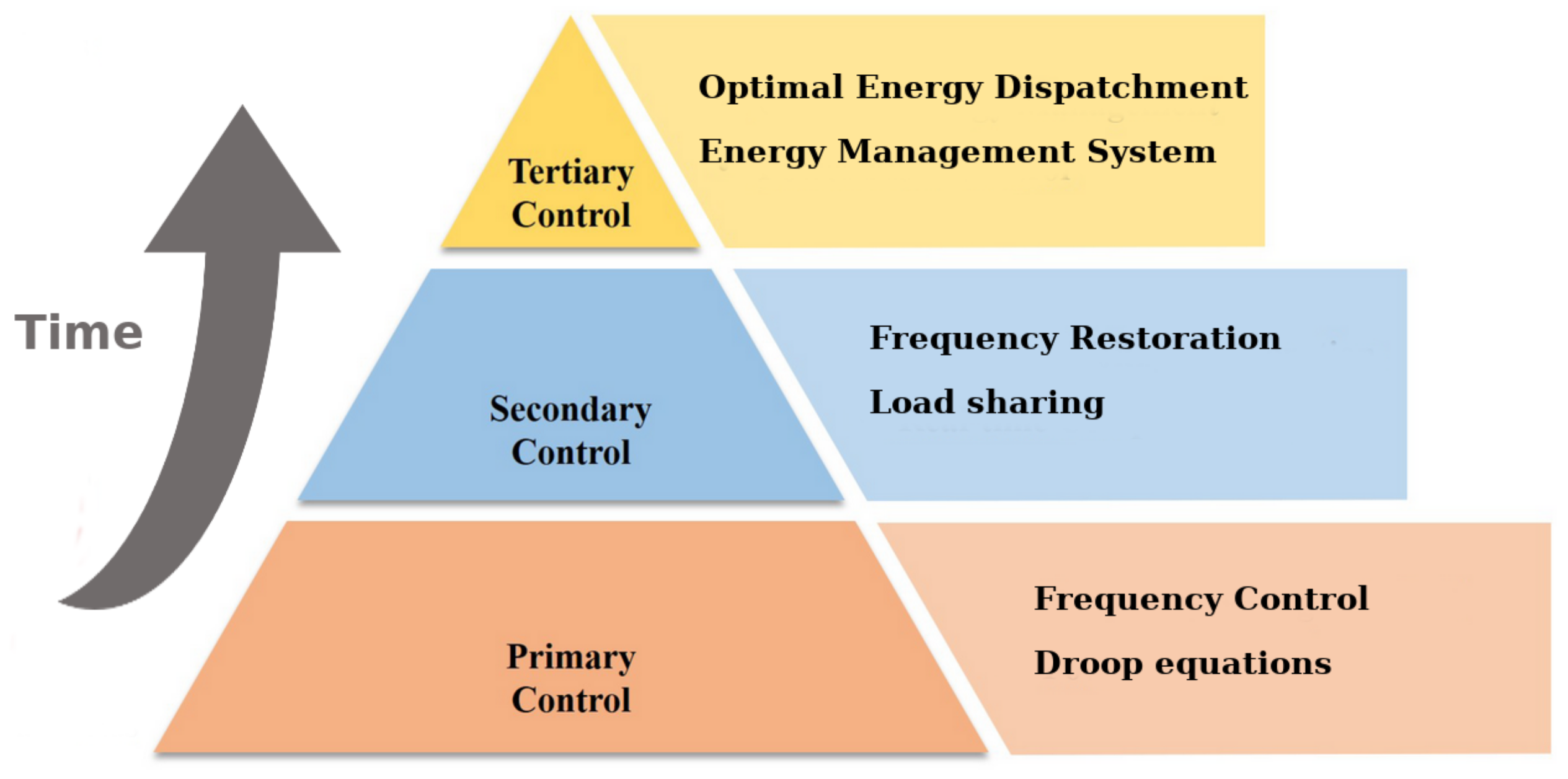
As already discussed, microgrids can operate in grid-connected or islanded modes. If the microgrid works in the filigree-connected mode, the generators inject power past following economical logics, while the frequency and voltage are kept in the correct range by the chief electrical grid. On the contrary, if it operates in islanded mode; the generators accept to guarantee voltage and frequency regulation. The control of the electrical grid is normally schematized into three levels, as shown in Figure 2:
-
Primary Control: aimed at restoring the imbalance between generation and load by irresolute the frequency of the power arrangement. In inverter-based microgrids, this is achieved through droop equations; information technology is the fastest among the 3 levels.
-
Secondary Control: aimed at restoring the nominal value of the frequency and the power exchange among the power systems. Information technology acts at longer time.
-
Tertiary Control: aimed at optimizing the economic aspects of load sharing, usually through an Free energy Direction System (Ems).
Both in islanded and grid-continued modes, Ems tin periodically send the power setpoints to the generators through the command network past using dissimilar protocols. To jeopardize the control of the electrical grid acting in grid-continued mode tin cause economic damages or fifty-fifty, in some cases, afflict the stability of the whole filigree. In islanded mode, attacking command mechanism is a severe threat to the grid stability.
In inverter-based microgrids, secondary control can be based on advice schemes. In these cases, attacks against the communication infrastructure can have astringent consequences on the availability of the whole microgrid. The dynamic of electromagnetic system physics is and then fast that the attacks targeting secondary control cannot be recognized in time by an IDS to allow the effective deployment of countermeasures. Moreover, these communication-based schemes are vulnerable to unaddressed cryptography attacks, such equally DoS attacks. On the other paw, the control of electric grids is essential for the service continuity. Resilience is topical in this field.
A cyber-assail resilient command strategy for islanded microgrids is presented in Reference [46]. The proposed control strategy realizes the detection and isolation of corrupted communication links and controllers in a microgrid whose secondary control is based on a distributed command system. A distributed resilient command strategy for frequency/voltage restoration, off-white real power sharing, and state-of-charge balancing in microgrids with multiple Energy Storage Systems in abnormal conditions is presented in Reference [47]. Reference [48] studies the affect of diverse kinds of cyber-attacks, such as false data injection [49], DoS [50], and replay attacks [51], on communication links based on CANBus for secondary command of the distributed generators. Reference [48] also proposes a mitigation strategy based on a reconfigurable secondary command machinery. Reference [52] introduces a command strategy able to mitigate fake data injection and DoS attacks, demonstrating the stability by using the Lyapunov theory nether different scenarios, with and without false data injection, and DoS attacks. Reference [53] proposes a distributed optimal frequency command for microgrids resilient confronting cyber attacks on status that they are within certain ranges, by introducing an auxiliary networked system interconnecting with the original cooperative control arrangement.
Microgrids can present dissimilar DER scenarios, including dissimilar types of non-programmable and programmable sources. Non-programmable sources can, anyhow, participate to the voltage control past injecting reactive power into the grid. Given the variety of scenarios and the complexity of the interactions of multiple sources participating to frequency control, voltage control, or both, there are still some unaddressed issues in the state of the art to be investigated.
8. Conclusions
In the nowadays work, the application of some of the well-nigh promising engineering for Industrial Control System to the Smart Microgrid environs has been discussed. These technologies present unlike maturity levels: while some are addressed by standards, such every bit in the IEC 62351, others require much more effort for the effective implementation in electrical power systems. SDN decouples the data and control plane and allows controlling an entire data network, thus assuring the action of access control, equally well as of congestion abstention schemes. Having a centralized control besides allows implementing a Network Intrusion Detection Organisation (NIDS) straight in the SDN controller and improving microgrid resiliency against cyber attacks and faults. The drawback of using SDN stands in the possible delay introduced past these actions, which could be incompatible with some actions required in an industrial surround. If most NIDS implementation are already commercial tools, Host IDS (HIDS) may stand for an improvement, particularly if they act in real-time. Real-fourth dimension HIDS may use information locally available at the host, such as CPU and retentiveness, system calls, loaded modules and libraries, user beliefs, and information nearly interfaces, to find anomalies. The chief trouble is the time necessary for these algorithms to run and the requested computational ability, peradventure not available in the industrial terminals where HIDS should act. One of the more interesting inquiry activities concerning the security of smart microgrids and, more than mostly, of ICS is represented by schemes able to detect abnormal concrete behaviors based on measures extracted past the industrial process. Anomaly tin can be divers as something that deviates from what is standard, normal, or expected. In the context of physics-based bibelot detection, it is an undesired physical working condition of the process, a departure of the process from a known working status defined every bit normal, or every bit an impossible observation of the state of the process because of an incoherence of the measurements. This definition includes working conditions caused by either faults or malicious manumissions of control devices, actuators, and sensors. In the field of industrial processes, and peculiarly in power systems, typical bibelot detection strategies are based on the dynamic state interpretation. Even if efficient, this approach requires the knowledge of the exact beliefs of the organisation. Machine Learning (ML) approaches could be useful to confront upward this problem. In the field of cyber-physical systems anomaly detection, it is quite mutual not to have a dataset containing examples of bad physical beliefs during a cyber attack. So, information technology is mandatory to utilize algorithms that tin can "learn" a behavior considered to be normal and classify new examples. The terminal promising research field discussed in the paper is represented by resilient control strategies. The command of electrical grids is essential for the service continuity. Both in islanded and grid-continued modes, taking control of the electric grid can cause peachy amercement and too affect the stability of the whole grid. Resilience is essential in this field. Further inquiry is necessary to develop commercial products to exist used in the field, but results from simulations and prototypes are actually promising.
Author Contributions
Conceptualization, G.B.G., P.G., and M.M.; methodology, G.B.1000. and M.Chiliad.; formal assay, G.B.G. and Thousand.Chiliad.; investigation, G.B.G.; resource, P.G. and Grand.Grand.; data curation, K.B.1000.; writing—original draft grooming, M.B.G.; writing—review and editing, M.Grand.; visualization, Thou.B.G.; supervision, M.Yard.; project administration, P.G.; funding conquering, P.Chiliad. All authors take read and agreed to the published version of the manuscript.
Funding
This research received no external funding.
Institutional Review Board Statement
Not applicable.
Informed Consent Argument
Non applicative.
Data Availability Argument
Not applicable.
Conflicts of Interest
The authors declare no conflict of interest.
Abbreviations
The following abbreviations are used in this manuscript:
| ICT | Information and Communication Engineering science |
| SM | Smart Microgrid |
| DER | Distributed Energy Resources |
| SCADA | Supervisory Control And Data Acquisition |
| MMS | Manufacturing Bulletin Specification |
| GOOSE | Generic Object Oriented Substation Event |
| SVM | Sampled Measured Values |
| SDN | Software Defined Network |
| ICS | Industrial Control Systems |
| NFV | Network Role Virtualization |
| PLC | Programmable Logic Controller |
| IDS | Intrusion Detection Organization |
| NIDS | Network Intrusion Detection Organization |
| HIDS | Host Intrusion Detection Arrangement |
| DoS | Denial of Service |
| IPS | Intrusion Prevention System |
| RTOS | Real-Time Operating Systems |
| RTU | Remote Final Unit |
| EMS | Energy Management Arrangement |
| PV | Photovoltaic |
References
- Falliere, N.; Murchu, 50.O.; Chien, E. W32.Stuxnet Dossier; Symantec Security Response; Symantec Corp.: Tempe, AZ, USA, 2011; Volume 5, p. 29. [Google Scholar]
- Bencsáth, B.; Pék, Thou.; Buttyán, L.; Felegyhazi, Thousand. The cousins of stuxnet: Duqu, flame, and gauss. Time to come Internet 2012, 4, 971–1003. [Google Scholar] [CrossRef]
- Case, D.U. Analysis of the Cyber Assail on the Ukrainian Ability Grid; Electricity Information Sharing and Analysis Heart (E-ISAC): Washington, DC, USA, 2016; p. 388. [Google Scholar]
- Liu, Ten.; Shahidehpour, One thousand.; Cao, Y.; Wu, L.; Wei, W.; Liu, X. Microgrid risk analysis considering the impact of cyber attacks on solar PV and ESS command systems. IEEE Trans. Smart Grid 2016, 8, 1330–1339. [Google Scholar] [CrossRef]
- Qi, J.; Hahn, A.; Lu, X.; Wang, J.; Liu, C.C. Cybersecurity for distributed energy resources and smart inverters. IET Cyber-Phys. Syst. Theory Appl. 2016, 1, 28–39. [Google Scholar] [CrossRef]
- Hossain, E.; Kabalci, E.; Bayindir, R.; Perez, R. Microgrid testbeds around the world: State of art. Energy Convers. Manag. 2014, 86, 132–153. [Google Scholar] [CrossRef]
- Lee, A. Electric Sector Failure Scenarios and Impact Analyses; Electric Power Inquiry Constitute: Palo Alto, CA, USA, 2013; Volume ane. [Google Scholar]
- Wang, Westward.; Lu, Z. Cyber security in the smart grid: Survey and challenges. Comput. Netw. 2013, 57, 1344–1371. [Google Scholar] [CrossRef]
- Yan, Y.; Qian, Y.; Sharif, H.; Tipper, D. A survey on cyber security for smart grid communications. IEEE Commun. Surv. Tutor. 2012, 14, 998–1010. [Google Scholar] [CrossRef]
- El Mrabet, Z.; Kaabouch, Due north.; El Ghazi, H.; El Ghazi, H. Cyber-security in smart grid: Survey and challenges. Comput. Electr. Eng. 2018, 67, 469–482. [Google Scholar] [CrossRef]
- Nejabatkhah, F.; Li, Y.W.; Liang, H.; Ahrabi, R.R. Cyber-Security of Smart Microgrids: A Survey. Energies 2021, 14, 27. [Google Scholar] [CrossRef]
- Canaan, B.; Colicchio, B.; Ould Abdeslam, D. Microgrid cyber-security: Review and challenges toward resilience. Appl. Sci. 2020, 10, 5649. [Google Scholar] [CrossRef]
- Volkova, A.; Niedermeier, Chiliad.; Basmadjian, R.; de Meer, H. Security challenges in control network protocols: A survey. IEEE Commun. Surv. Tutor. 2018, 21, 619–639. [Google Scholar] [CrossRef]
- Bani-Ahmed, A.; Weber, Fifty.; Nasiri, A.; Hosseini, H. Microgrid communications: State of the art and future trends. In Proceedings of the 2014 International Briefing on Renewable Energy Research and Application (ICRERA), Milwaukee, WI, Usa, 19–22 October 2014; pp. 780–785. [Google Scholar]
- Reda, H.T.; Ray, B.; Peidaee, P.; Anwar, A.; Mahmood, A.; Kalam, A.; Islam, N. Vulnerability and Impact Analysis of the IEC 61850 GOOSE Protocol in the Smart Filigree. Sensors 2021, 21, 1554. [Google Scholar] [CrossRef]
- Kang, B.; Maynard, P.; McLaughlin, M.; Sezer, South.; Andrén, F.; Seitl, C.; Kupzog, F.; Strasser, T. Investigating cyber-physical attacks against IEC 61850 photovoltaic inverter installations. In Proceedings of the 2015 IEEE 20th Conference on Emerging Technologies & Factory Automation (ETFA), Luxembourg, 8–11 September 2015; pp. 1–8. [Google Scholar]
- Schlegel, R.; Obermeier, Southward.; Schneider, J. A security evaluation of IEC 62351. J. Inf. Secur. Appl. 2017, 34, 197–204. [Google Scholar] [CrossRef]
- Hussain, S.S.; Ustun, T.Southward.; Kalam, A. A review of IEC 62351 security mechanisms for IEC 61850 message exchanges. IEEE Trans. Ind. Inform. 2019, sixteen, 5643–5654. [Google Scholar] [CrossRef]
- Ustun, T.S.; Hussain, Due south.S. IEC 62351-iv Security Implementations for IEC 61850 MMS Messages. IEEE Access 2020, 8, 123979–123985. [Google Scholar] [CrossRef]
- Hussain, S.South.; Farooq, S.Grand.; Ustun, T.Due south. Assay and implementation of message hallmark code (MAC) algorithms for GOOSE message security. IEEE Access 2019, vii, 80980–80984. [Google Scholar] [CrossRef]
- Farooq, Southward.Thou.; Hussain, S.Due south.; Ustun, T.Due south. Operation evaluation and assay of IEC 62351-half dozen probabilistic signature scheme for securing GOOSE letters. IEEE Access 2019, 7, 32343–32351. [Google Scholar] [CrossRef]
- Hu, F.; Hao, Q.; Bao, Thou. A survey on software-defined network and openflow: From concept to implementation. IEEE Commun. Surv. Tutor. 2014, 16, 2181–2206. [Google Scholar] [CrossRef]
- Rehmani, M.H.; Davy, A.; Jennings, B.; Assi, C. Software defined networks-based smart grid advice: A comprehensive survey. IEEE Commun. Surv. Tutor. 2019, 21, 2637–2670. [Google Scholar] [CrossRef]
- Ren, L.; Qin, Y.; Wang, B.; Zhang, P.; Luh, P.B.; Jin, R. Enabling resilient microgrid through programmable network. IEEE Trans. Smart Grid 2016, 8, 2826–2836. [Google Scholar] [CrossRef]
- Piedrahita, A.F.One thousand.; Gaur, V.; Giraldo, J.; Cardenas, A.A.; Rueda, S.J. Leveraging software-defined networking for incident response in industrial command systems. IEEE Softw. 2017, 35, 44–50. [Google Scholar] [CrossRef]
- Genge, B.; Graur, F.; Haller, P. Experimental assessment of network design approaches for protecting industrial control systems. Int. J. Crit. Infrastruct. Prot. 2015, xi, 24–38. [Google Scholar] [CrossRef]
- Sándor, H.; Genge, B.; Szántó, Z.; Márton, L.; Haller, P. Cyber attack detection and mitigation: Software defined survivable industrial control systems. Int. J. Crit. Infrastruct. Prot. 2019, 25, 152–168. [Google Scholar] [CrossRef]
- Yang, J.; Zhou, C.; Tian, Y.C.; Yang, Due south.H. A software-divers security approach for securing field zones in industrial control systems. IEEE Access 2019, 7, 87002–87016. [Google Scholar] [CrossRef]
- Jin, D.; Li, Z.; Hannon, C.; Chen, C.; Wang, J.; Shahidehpour, M.; Lee, C.W. Toward a cyber resilient and secure microgrid using software-divers networking. IEEE Trans. Smart Filigree 2017, 8, 2494–2504. [Google Scholar] [CrossRef]
- Fausto, A.; Marchese, M. Implementation details to reduce the latency of an SDN Statistical Fingerprint-Based IDS. In Proceedings of the 2019 International Symposium on Advanced Electrical and Communication Technologies (ISAECT), Rome, Italy, 27–29 Nov 2019; pp. 1–6. [Google Scholar]
- Danzi, P.; Angjelichinoski, Thousand.; Stefanović, Č.; Dragičević, T.; Popovski, P. Software-defined microgrid control for resilience against denial-of-service attacks. IEEE Trans. Smart Filigree 2018, x, 5258–5268. [Google Scholar] [CrossRef]
- Li, Y.; Qin, Y.; Zhang, P.; Herzberg, A. SDN-enabled cyber-physical security in networked microgrids. IEEE Trans. Sustain. Energy 2018, 10, 1613–1622. [Google Scholar] [CrossRef]
- Haas, Z.J.; Culver, T.L.; Sarac, K. Vulnerability Challenges of Software Defined Networking. IEEE Commun. Mag. 2021, 59, 88–93. [Google Scholar] [CrossRef]
- Liu, M.; Xue, Z.; Xu, X.; Zhong, C.; Chen, J. Host-based intrusion detection system with organization calls: Review and time to come trends. ACM Comput. Surv. (CSUR) 2018, 51, ane–36. [Google Scholar] [CrossRef]
- Martinez, C.V.; Vogel-Heuser, B. A host intrusion detection system architecture for embedded industrial devices. J. Frankl. Inst. 2019, 358, 210–236. [Google Scholar] [CrossRef]
- Vargas, C.; Langfinger, M.; Vogel-Heuser, B. A tiered security analysis of industrial control system devices. In Proceedings of the 2017 IEEE 15th International Briefing on Industrial Information science (INDIN), Emden, Federal republic of germany, 24–26 July 2017; pp. 399–404. [Google Scholar]
- Giraldo, J.; Urbina, D.; Cardenas, A.; Valente, J.; Faisal, M.; Ruths, J.; Tippenhauer, N.O.; Sandberg, H.; Candell, R. A survey of physics-based assault detection in cyber-physical systems. ACM Comput. Surv. (CSUR) 2018, 51, ane–36. [Google Scholar] [CrossRef]
- Pimentel, G.A.; Clifton, D.A.; Clifton, L.; Tarassenko, Fifty. A review of novelty detection. Signal Process. 2014, 99, 215–249. [Google Scholar] [CrossRef]
- Shi, D.; Lin, P.; Wang, Y.; Chu, C.C.; Xu, Y.; Wang, P. Charade Attack Detection of Isolated DC Microgrids nether Consensus-Based Distributed Voltage Command Architecture. IEEE J. Emerg. Sel. Top. Circ. Syst. 2021, 11, 155–167. [Google Scholar] [CrossRef]
- Chavez, A.; Lai, C.; Jacobs, Northward.; Hossain-McKenzie, Southward.; Jones, C.B.; Johnson, J.; Summers, A. Hybrid Intrusion Detection Arrangement Design for Distributed Energy Resources Systems. In Proceedings of the 2019 IEEE CyberPELS (CyberPELS), Knoxville, TN, The states, 29 April–ane May 2019; pp. ane–6. [Google Scholar]
- Kosek, A.G. Contextual bibelot detection for cyber-concrete security in smart grids based on an artificial neural network model. In Proceedings of the 2016 Articulation Workshop on Cyber-Concrete Security and Resilience in Smart Grids (CPSR-SG), Vienna, Austria, 12 April 2016; pp. ane–six. [Google Scholar]
- Li, F.; Xie, R.; Yang, B.; Guo, L.; Ma, P.; Shi, J.; Ye, J.; Song, W. Detection and identification of cyber and physical attacks on distribution power grids with pvs: An online high-dimensional data-driven approach. IEEE J. Emerg. Sel. Top. Power Electron. 2019. [Google Scholar] [CrossRef]
- Shilay, D.M.; Lorey, K.M.; Weiz, T.; Lovetty, T.; Cheng, Y. Catching Anomalous Distributed Photovoltaics: An Edge-based Multi-modal Anomaly Detection. arXiv 2017, arXiv:1709.08830. [Google Scholar]
- Gaggero, G.B.; Rossi, M.; Girdinio, P.; Marchese, Thousand. Detecting Organisation Fault/Cyberattack within a Photovoltaic Organization Connected to the Grid: A Neural Network-Based Solution. J. Sens. Actuator Netw. 2020, 9, 20. [Google Scholar] [CrossRef]
- Fotiadou, K.; Velivassaki, T.H.; Voulkidis, A.; Skias, D.; De Santis, C.; Zahariadis, T. Proactive Critical Free energy Infrastructure Protection via Deep Feature Learning. Energies 2020, 13, 2622. [Google Scholar] [CrossRef]
- Zhou, Q.; Shahidehpour, M.; Alabdulwahab, A.; Abusorrah, A. A cyber-attack resilient distributed control strategy in islanded microgrids. IEEE Trans. Smart Grid 2020, xi, 3690–3701. [Google Scholar] [CrossRef]
- Deng, C.; Wang, Y.; Wen, C.; Xu, Y.; Lin, P. Distributed resilient control for free energy storage systems in cyber—Physical microgrids. IEEE Trans. Ind. Inform. 2020, 17, 1331–1341. [Google Scholar] [CrossRef]
- Rath, South.; Pal, D.; Sharma, P.S.; Panigrahi, B.K. A Cyber-Secure Distributed Control Compages for Autonomous Ac Microgrid. IEEE Syst. J. 2020. [Google Scholar] [CrossRef]
- Liu, Y.; Ning, P.; Reiter, Thousand.K. False data injection attacks against state estimation in electric power grids. ACM Trans. Inf. Syst. Secur. (TISSEC) 2011, 14, one–33. [Google Scholar] [CrossRef]
- Hussain, A.; Heidemann, J.; Papadopoulos, C. A framework for classifying denial of service attacks. In Proceedings of the 2003 Briefing on Applications, Technologies, Architectures, and Protocols for Estimator Communications, Karlsruhe, Deutschland, 25–29 August 2003; pp. 99–110. [Google Scholar]
- Hosseinzadeh, M.; Sinopoli, B.; Garone, E. Feasibility and detection of replay assail in networked constrained cyber-physical systems. In Proceedings of the 57th Annual Allerton Conference on Communication, Control, and Computing (Allerton), Monticello, IL, USA, 24–27 September 2019; pp. 712–717. [Google Scholar]
- Zhou, Q.; Shahidehpour, 1000.; Alabdulwahab, A.; Abusorrah, A.; Che, L.; Liu, 10. Cantankerous-Layer Distributed Control Strategy for Cyber Resilient Microgrids. IEEE Trans. Smart Grid 2021. [Google Scholar] [CrossRef]
- Liu, Y.; Li, Y.; Wang, Y.; Zhang, Ten.; Gooi, H.B.; Xin, H. Robust and Resilient Distributed Optimal Frequency Command for Microgrids Against Cyber Attacks. IEEE Trans. Ind. Inform. 2021. [Google Scholar] [CrossRef]
Effigy 1. Multi-Layered SDN-enabled Microgrid architecture.
Figure 1. Multi-Layered SDN-enabled Microgrid architecture.
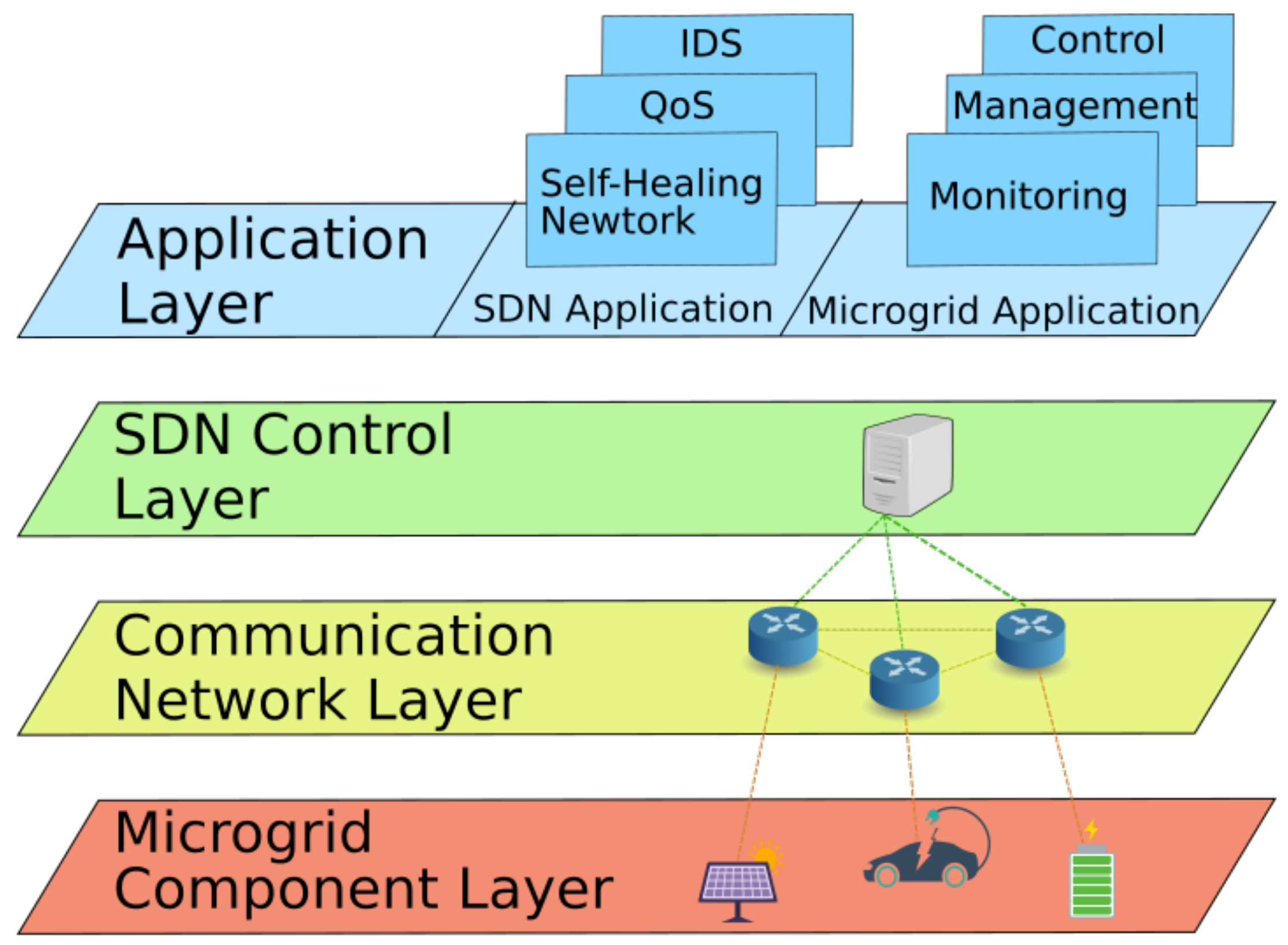
Figure 2. Control levels of the electrical grid.
Figure 2. Command levels of the electrical grid.
Tabular array 1. Summary of IEC 62351 specifications.
Tabular array 1. Summary of IEC 62351 specifications.
| Section | Description |
|---|---|
| Role 1 | Introduction to security issue |
| Office 2 | Glossary of terms |
| Office 3 | Profiles including TCP/IP |
| Part 4 | Profiles including MMS and derivatives |
| Part five | Security for IEC 60870-five and derivatives |
| Part 6 | Security for IEC 61850 |
| Part 7 | Network and system management (NSM) data object models |
| Office eight | Office-based access command for power system management |
| Part 9 | Cyber security cardinal management for power arrangement equipment |
| Part 10 | Security architecture guidelines |
| Part 11 | Security for eXtensible markup language (XML) documents |
| Function 12 | Resilience and security recommendations for power systems with DER cyber-physical systems |
| Part 13 | Guidelines on security topics to be covered in standards and specifications |
| Office 90-one | Guidelines for handling role-based access command in ability systems |
| Part 90-2 | Deep packet inspection of encrypted communications |
| Part ninety-iii | Guidelines for network and organisation direction |
| Part 100-1 | Conformance test cases for IEC TS 62351-five and IEC TS 60870-5-7 |
| Part 100-3 | Conformance test cases for the IEC 62351-3, the secure communication extension for profiles including TCP/IP |
Table ii. IDS classification.
Table 2. IDS classification.
| IDS Classification | ||
|---|---|---|
| By monitored element | Network-IDS | Host-IDS |
| Past actions | Passive (IDS) | Active (IDS and IPS) |
| By detection methods | Signature-based | Anomaly-based |
| Publisher's Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This commodity is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC Past) license (https://creativecommons.org/licenses/past/four.0/).
Source: https://www.mdpi.com/2076-3417/11/16/7363/htm
0 Response to "Microgrid Communications State of the Art and Future Trends Pdf"
Post a Comment